Tenant Provisioning
The topics in this section describe how to configure Portal for ArcGIS for use with ArcFM XI products. A tenant provides a unique identifier for your organization and allows your users to access the hosted components of the ArcFM solution.
App Registration
As part of the tenant configuration process, you must register the Auth0 service in your Portal to authenticate users. The advantage of this registration is that it allows existing users signing into ArcFM to be automatically authenticated to feature services. Refer to Esri’s Add and register an app article for more information.
Follow these steps to add and register the Auth0 application:
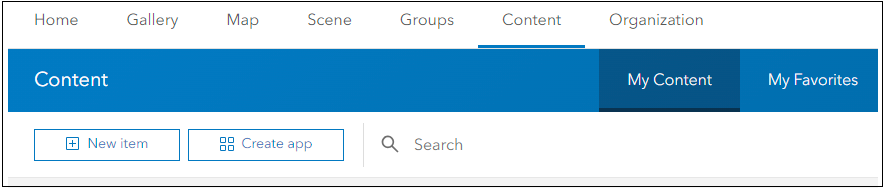
- Log in to your Portal for ArcGIS account and click Content.
- Ensure that My Content is highlighted. Under the Content heading, click New Item.
- Click Application, and under Application Type, click Other application then click Next.
- Type a descriptive Title.
- Select the organizational folder to save the item.
- Create a Tag called arcfm.IMPORTANT: Since these portal group names are matched to product roles, you must add this tag. It allows the portal groups to be seen across the ArcFM products licensed to your organization.
- Type a Summary, which is extremely helpful for searching,
then click Next.
The app is added, and the Application Overview window opens. The Auth0 application is listed in the My Content section.
Follow these steps to register the Auth0 application:
-
Select the Auth0 application you just created.
-
In the upper right corner, click Settings.
-
Under Application, click Update.
-
In the window that opens, type the Redirect URI:
https://arcfm{TenantName}.Auth0.com/login/callback, https://arcfm{TenantName}.Auth0.com/mobileIMPORTANT: The {TenantName} is provided by Schneider Electric when tenant resources are deployed. -
Click Add, then click Update.
-
Review the configuration and click Save.
Provide the following: the group names you created, the AppID and AppSecret from the App Registration section, and your Portal URL, to arcfmreadiness@se.com. Schneider Electric then completes the authentication and configuration process.
Group Membership
Similar to other ArcFM XI products, Designer XI uses groups to assign roles to users. Refer to Esri’s Create groups in Portal for ArcGIS article for more information about groups.
Follow these steps to create your groups:
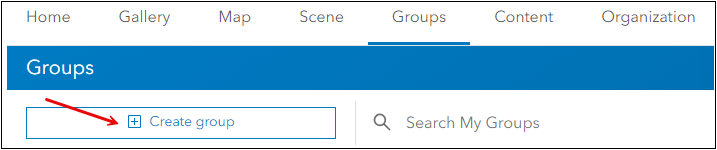
- Log in to your Portal for ArcGIS account.
- On the top menu, click Groups.
- Under Groups, click Create Group.
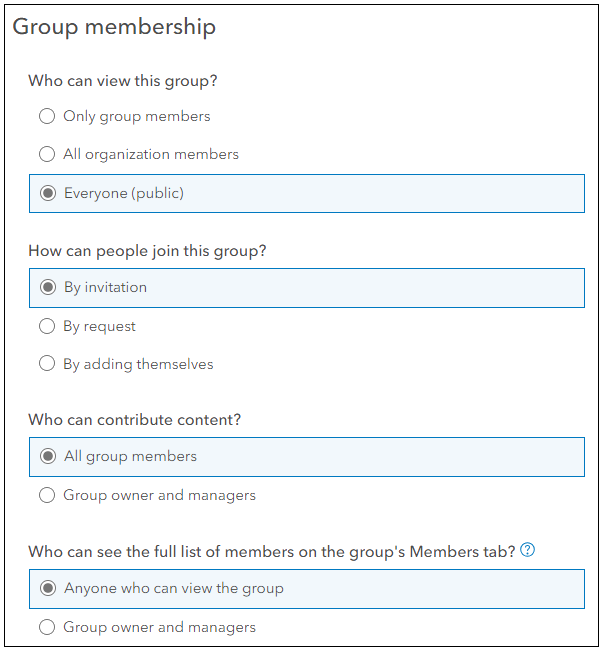
- Under Group overview, type a Name, Summary, and provide useful Tags.
- Select the Group membership options applicable to your organization.
- Under Group designations, enable Shared update and Administrative group, if applicable, and click Save.
- Create additional groups using the same options that correspond
to these roles:
- Designer Admin
- Designer Designer
- Designer Approver
- Refer to the Client Configuration Mapping topic to map your Portal groups to app-specific roles.
The group names listed above are suggestions, so your organization can create groups according to your naming conventions. For more about roles and capabilities, refer to the ArcFM Solution XI Series Named User Functionality Matrix article on myArcFM.
SAML-Compliant Identity Provider Configuration
The configuration of a SAML-Compliant Identity Provider is critical in order to ensure your ArcGIS Enterprise Environment is properly connecting to an ArcFM tenant. This is a required step in the implementation of ArcFM.
Security Assertion Markup Language (SAML) is an open standard that is used to securely exchange authentication and authorization data between an organization-specific identity provider and a service provider (in this case, your ArcGIS Enterprise organization). This approach is known as SAML Web Single Sign On.
ArcFM is compliant with SAML 2.0 and integrates with identity providers that support SAML 2 Web Single Sign On. The advantage of setting up SAML is that you do not need to create additional logins for access to your ArcGIS Enterprise organization. Users instead use their existing login credentials previously configured in an identity store. This process is referred to throughout the documentation as setting up organization-specific logins. Refer to Esri’s Configure a SAML-compliant identity provider with a portal article for full instructions.